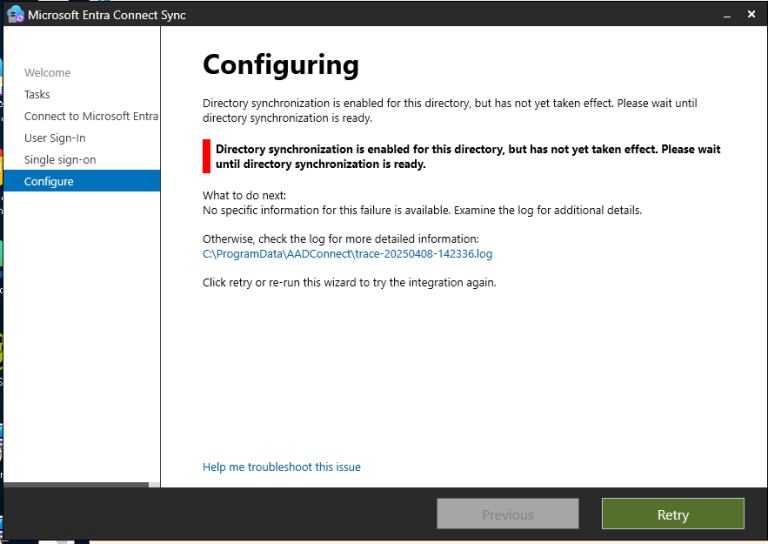
Entra ID Connect: directory synchronization is enabled for this directory, but has not yet taken effect.
Directory synchronization is enabled for this directory but has not yet taken effect. Today i created a new tenant and configured Entra ID connect sync. After a wait of approx more then 72 hours. In fact i waited more then 2 weeks. This error returned everytime i wanted to make a change to the Entra…
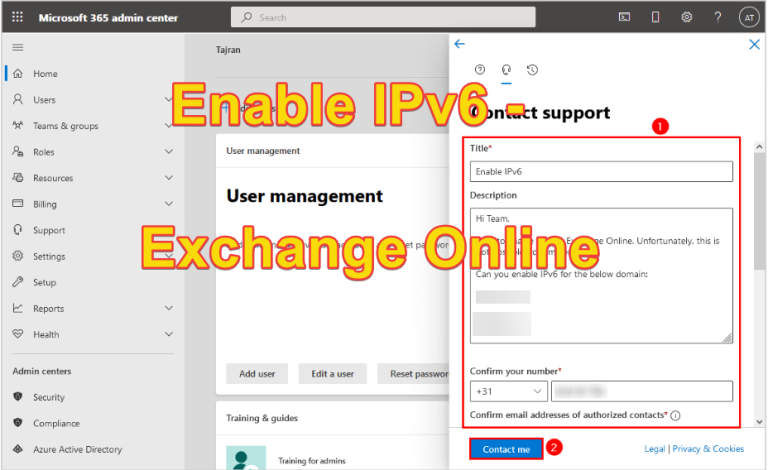
Guide – Enable IPv6 Exchange Online
By default, IPv6 is not activated in Microsoft 365’s Exchange Online for tenant configurations. If you’re looking to enable IPv6 for inbound email in Exchange Online, you might have noticed that there isn’t a straightforward option available to do so. Does this mean it’s impossible? Not necessarily. This article will guide you through the steps…

Guide – Password rotation Seamless SSO – AzureADSSO Account
Introduction The purpose is to check that password rotation is in place with Azure AD SSO Technical explanation:AzureAD SSO is performed using a gateway. This gateway converts a Kerberos TGS ticket to a SAML ticket.In short, a connection is made to the computer account AZUREADSSOACC and the secret of this user account is used as…
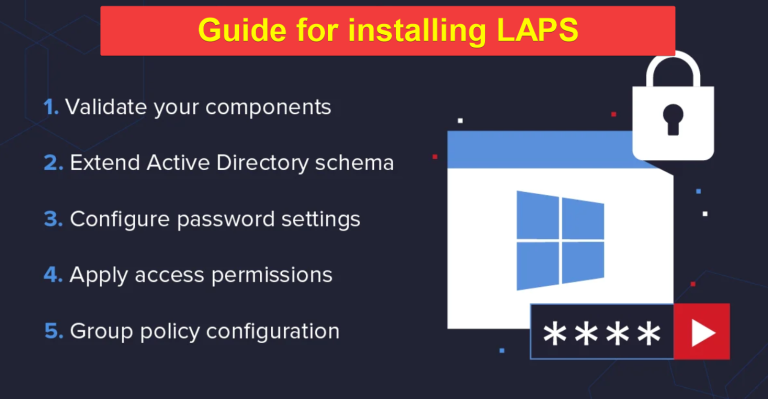
LAPS Installation / implementation (Local Administrator Password Solutions) – Guide
WHY use LAPS? Windows Local Administrator Password Solution (LAPS) is designed to address the issue of poor management and security of local administrator passwords in a Windows environment. These are the main problems that LAPS solves: In summary, Windows LAPS addresses issues related to weak passwords, lack of password rotation, unauthorized access, and management complexity…
How to handle expired Active Directory accounts remain active in Entra ID
In a hybrid environment where an AAD Connect is configured to sync the onprem/classic Active directory and its users to Azure Active Directory, the expire date property in AD is not synced.This in itself is not that big of a deal, but the fact that an expired user in AD, that is blocked for use…

How to verify your domain’s Email security in 60 seconds
OK, It’s 2024 and we all know this means that Google, Yahoo, and others are scheduled to start tightening their rules on acceptance of non-authenticated emails. And you’ve probably been through the setup process for SPF, DKIM, and DMARC and are crossing your fingers that everything is working correctly and that your emails are making…
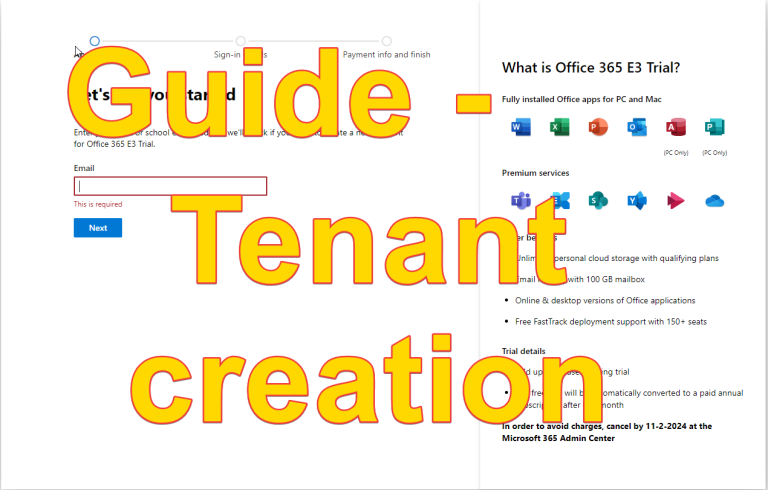
Guide – How you create your own Microsoft 365 / Azure Tenant
Welcome, I’ll guide you through setting up your very own Microsoft 365 / azure tenant. A tenant is the basic foundation to get started with Microsoft 365 or Microsoft Azure products. Create your own Microsoft 365 / Azure tenant First, launch an InPrivate Browser session; I recommend using Microsoft Edge for an optimal experienceThen, navigate…

Microsoft defender only scans a few files (full scan)
Today, we had an issue with a client’s device where the endpoint protection was only scanning about 200-300 files during a full system scan. The client was concerned because Microsoft Defender was issuing warnings on his device. Upon investigating, we discovered that all disk drives were set to be excluded in the endpoint protection settings…

5 easy ways to Make Microsoft Entra ID Accounts More Secure
The cloud is trending, and more and more applications and services depend on the cloud. A cloud environment offers many advantages but also introduces a number of new risks. Microsoft has sufficient solutions in its services to optimally use this security. Through this article, we will discuss a number of services that are available from…
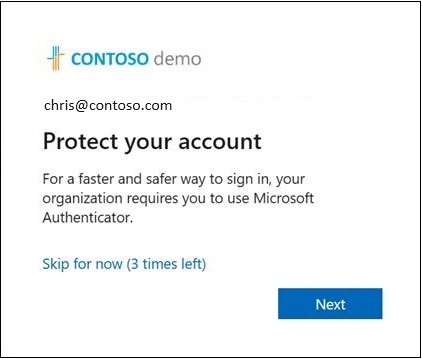
Microsoft MFA – Protect your account pop-up
When a user who can receive Authenticator push notifications hasn’t set it up yet, they’ll be encouraged to set up Authenticator push notifications to make signing in easier and more secure. It’s also possible that they’ll be asked to set up additional security measures. If you use Microsoft Authenticator or another token manager to create…
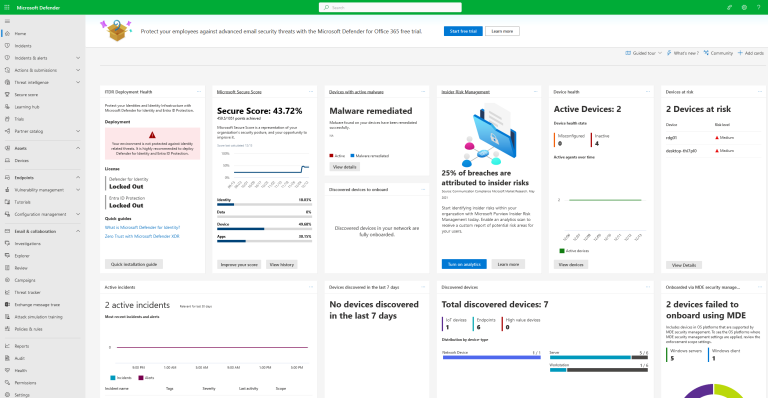
Common deployment mistakes in Microsoft Defender for Endpoint implementations
When initiating the deployment of Defender for Endpoint, it all commences with thorough preparation. It is crucial to conduct a comprehensive assessment of the existing environment to preempt policy conflicts and meticulously craft a solution that seamlessly aligns with the management methods, systems, and network configuration utilized within that specific environment. What are some of…
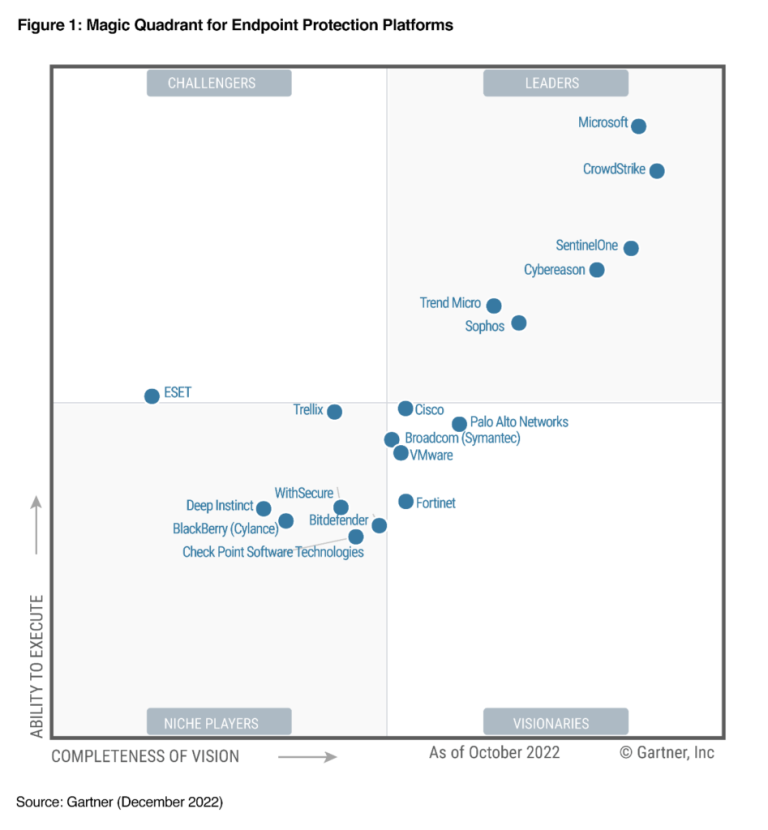
Microsoft has been recognized as a leading entity in the 2022 Gartner Magic Quadrant for Endpoint Protection Platforms.
The evolving landscape of cybersecurity presents ongoing challenges for global defenders. As hybrid work becomes a norm and novel threats like Ransomware as a Service emerge, organizations require a partner that offers not just advanced endpoint security but also a comprehensive solution aiding security teams in combating sophisticated attacks. Concurrently, organizations are mindful of budget…



