Category: Microsoft defender
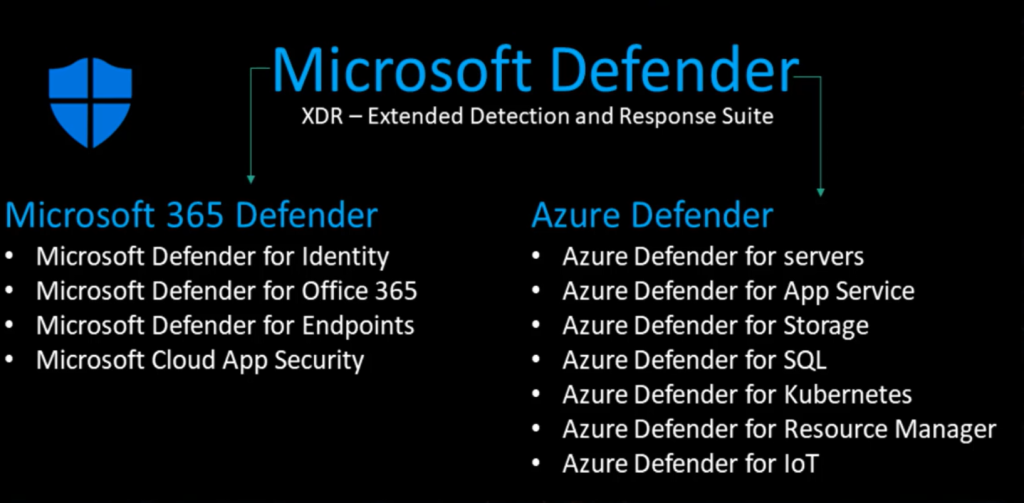
In this blog we’ll write and learn about different features and capabilities of the Microsoft 365 Defender Suite. Below you will see a diagram about varius forms and shapres of the 365 Defender suite. This will help you to connect the dots and create the intelligence that you need. I really hope that this blog will be informative to you
Defender for Cloud
Defender for Cloud is a Cloud-native application protection platform based on Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP).
Defender for Cloud offers multiple Defender plans:
- Defender for Servers
- Defender for App Service
- Defender for Database
- Defender for Storage
- Defender for Containers
- Defender for Key Vault
- Defender for Resource Manager
- Defender for DNS
- Defender CSPM
Defender for Servers
The Defender for Servers plan, a component of Defender for Cloud, offers two pricing tiers: P1 and P2. The P1 tier concentrates on a select range of defensive measures, predominantly emphasizing Defender for Endpoint technology. In contrast, the P2 tier encompasses the comprehensive range of enhanced security features from Defender for Cloud. This includes threat detection at the network layer, File Integrity Monitoring (FIM), the Qualys vulnerability assessment, and a complimentary data ingestion allowance of 500MB
P1=$5 Server / Month
P2=$15 Server / Month
Both P1/ P2 contain all features of Defender for Endpoint P2 (Except the vulnerability management add-on which is only part of the Defender for Servers P2, is in MDE available as an add-on)
Defender for Endpoint
Microsoft Defender for Endpoint (MDE) is a comprehensive solution for preventing, detecting, and automating the investigation and response to threats against endpoints.
Once the integration of Defender for Endpoint is activated in Defender for Cloud, machines will be provisioned accordingly. This setup and installation process is facilitated through Azure Policies, which include the onboarding script along with additional configurations. As a result, the MDE.Windows and MDE.Linux Virtual Machine (VM) extensions are deployed for systems running Windows Server 2012 R2 and later versions.
Azure Arc
Azure Arc serves as a link that extends Azure’s capabilities to on-premises environments and other cloud platforms, such as AWS and GCP. To connect servers with Azure Arc, it’s necessary to utilize Azure Arc-enabled servers and install the Azure Connected Machine agent on supported systems.
1: In Defender for Cloud
2: Is the plan Defender for Servers P1 or P2 enabled
3: Which onboards Defender for Endpoint P2 via Azure Policy
License for Defender for Endpoint is part of the Defender for Server plan – no additional license purchasing is needed.
Read more about the defender suite bellow

How to verify your domain’s Email security in 60 seconds
OK, It’s 2024 and we all know this means that Google, Yahoo, and others are scheduled to start tightening their rules on acceptance of non-authenticated emails. And you’ve probably been through the setup process for SPF, DKIM, and DMARC and are crossing your fingers that everything is working correctly and that your emails are making…

Microsoft defender only scans a few files (full scan)
Today, we had an issue with a client’s device where the endpoint protection was only scanning about 200-300 files during a full system scan. The client was concerned because Microsoft Defender was issuing warnings on his device. Upon investigating, we discovered that all disk drives were set to be excluded in the endpoint protection settings…
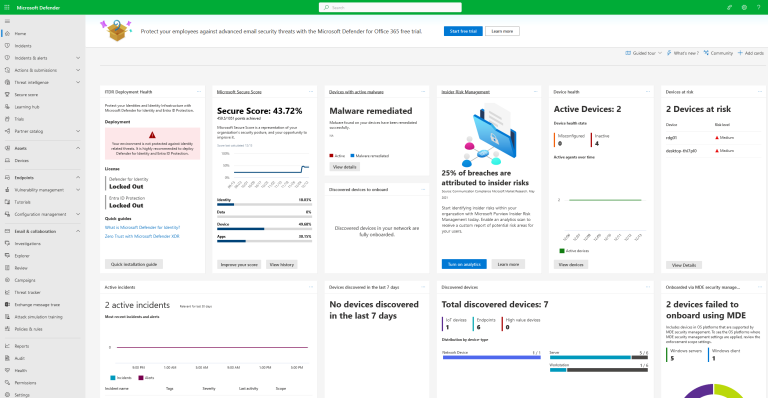
Common deployment mistakes in Microsoft Defender for Endpoint implementations
When initiating the deployment of Defender for Endpoint, it all commences with thorough preparation. It is crucial to conduct a comprehensive assessment of the existing environment to preempt policy conflicts and meticulously craft a solution that seamlessly aligns with the management methods, systems, and network configuration utilized within that specific environment. What are some of…
Guide – Getting started – Microsoft Defender for Endpoint
The following guide is crafted to assist you in initiating your journey with Microsoft Defender for Endpoint What are the Key Elements of Microsoft defender for endpoint ?Microsoft Defender for Endpoint comprises the following essential elements: Prerequisite Please note that Microsoft Defender for Endpoint has been split into two editions—Plan 1 and Plan 2. Plan…
Defender for endpoint – Web content filtering
Defender for Endpoint’s web content filtering is a crucial tool in countering attackers who frequently switch domains, especially when flagged as malicious. AiTM domains, often newly registered and short-lived, can be effectively managed using web content filtering in Microsoft Defender for Endpoint (MDE). Here’s how: With Defender for Endpoint – web content filtering’s help, you…

Azure AD / Entra ID – Identity suspicious logon behavior
In Azure AD, now referred to as Entra ID sing-in logs, the user’s sign-in IP and the location is logged. In the sign-in logs, you can see the IP of the location and, for apps like OfficeHome, the original IP becomes visible when there is a redirection in IP or URL. This information helps track…