Azure AD / Entra ID – Identity suspicious logon behavior
In Azure AD, now referred to as Entra ID sing-in logs, the user’s sign-in IP and the location is logged. In the sign-in logs, you can see the IP of the location and, for apps like OfficeHome, the original IP becomes visible when there is a redirection in IP or URL. This information helps track the user’s activity and any changes in IP or URL during the sign-in process.
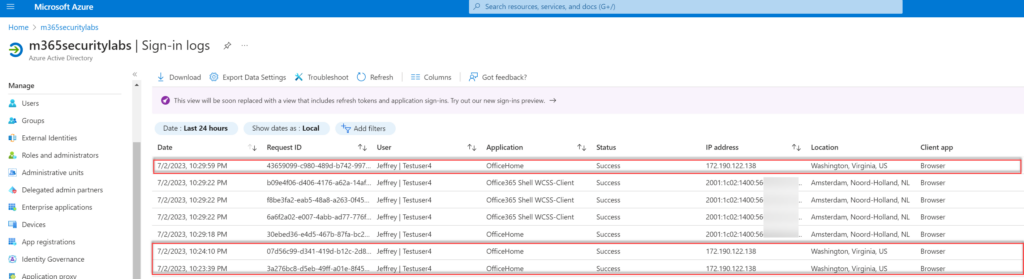
The rapid switching of IP addresses and locations could potentially trigger security events in Defender for Cloud Apps and Azure AD Identity Protection. These tools are designed to identify and respond to suspicious activities, helping to safeguard your accounts and data from unauthorized access or security threats.
MICROSOFT DEFENDER
The Entra ID has detected suspicious logon behavior associated with identity issues. There are signs of someone attempting to sign in from multiple countries within a short timeframe. This could indicate unauthorized access or potential security concerns related to your account.
let OfficeHomeSessionIds =
AADSignInEventsBeta
| where Timestamp > ago(1d)
| where ErrorCode == 0
| where ApplicationId == "4765445b-32c6-49b0-83e6-1d93765276ca" //OfficeHome application
| where ClientAppUsed == "Browser"
| where LogonType has "interactiveUser"
| summarize arg_min(Timestamp, Country) by SessionId;
AADSignInEventsBeta
| where Timestamp > ago(1d)
| where ApplicationId != "4765445b-32c6-49b0-83e6-1d93765276ca"
| where ClientAppUsed == "Browser"
| project OtherTimestamp = Timestamp, Application, ApplicationId, AccountObjectId, AccountDisplayName, OtherCountry = Country, SessionId
| join OfficeHomeSessionIds on SessionId
| where OtherTimestamp > Timestamp and OtherCountry != Country