Guide – Getting started – Microsoft Defender for Endpoint
The following guide is crafted to assist you in initiating your journey with Microsoft Defender for Endpoint
What are the Key Elements of Microsoft defender for endpoint ?
Microsoft Defender for Endpoint comprises the following essential elements:
Prerequisite
Please note that Microsoft Defender for Endpoint has been split into two editions—Plan 1 and Plan 2. Plan 2 contains all the features, while Plan 1 has only some of them. Learn more here .
– Create a microsoft 365 / microsoft azure tenant. Create here
– Choose between Microsoft Defender for endpoint plan 1 or Plan 2. choose here
– Assign the Microsoft defender for endpoint plan 1 or plan 2 license to the tenant. See here
Configure Microsoft defender for Endpoint
– login into your Microsoft 365 tenant (link) and go to the security portal by clicking on security. Or go directly here
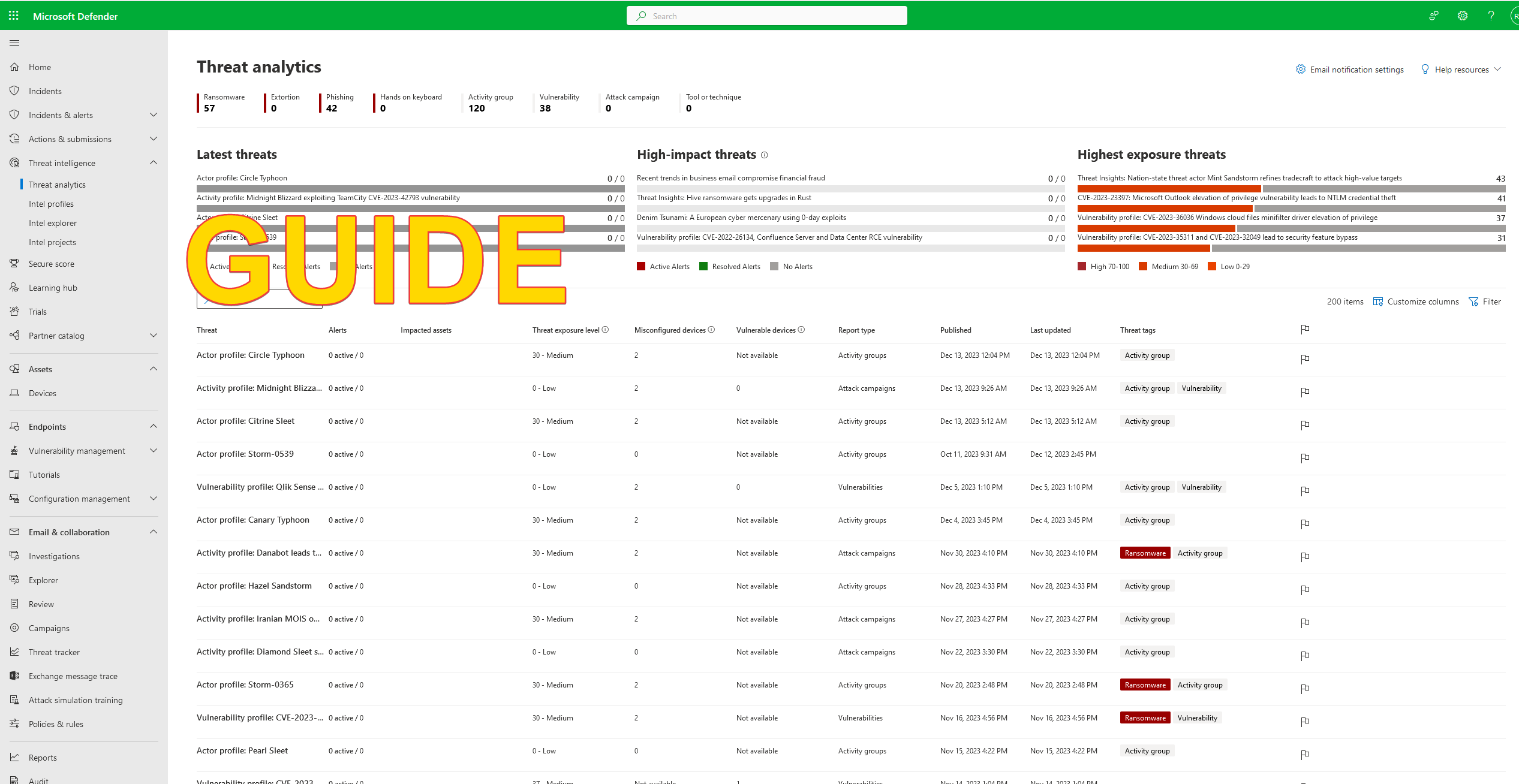
– Once in the security center go to the bottom of the menu and select Settings. You see the following page bellow (step1.)
– Click on Endpoints (step 2.)
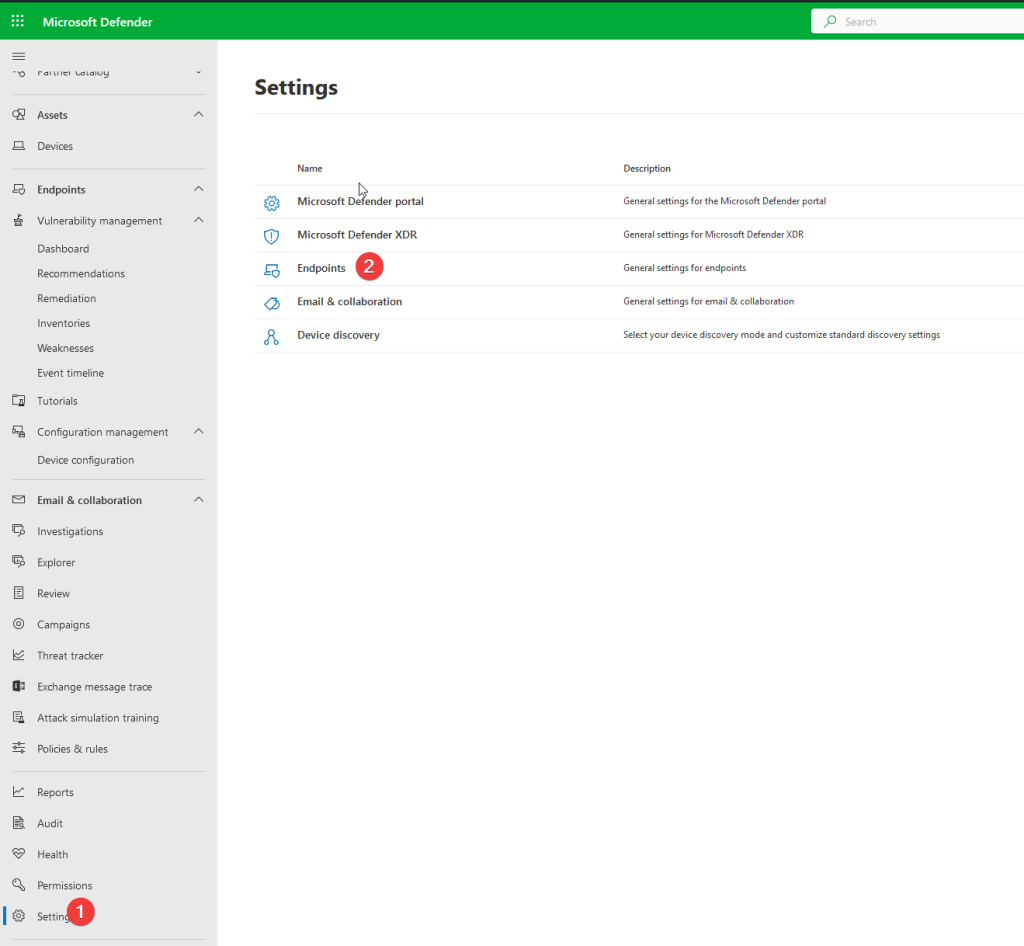
– Once on the endpoint settings page. Configure the following settings
Go to ->Generral – > advanced features
check if the following settings are on
Enable EDR in block mode – off
Allow or block file – on
Hide potential duplicate device records – on
Custom network indicators – off
Tamper protection – on
Show user details – on
Microsoft Defender for Cloud Apps -off
Web content filtering – off
Device discovery – on
Streamline connectivity during device onboarding (Preview) – off
Live Response -off
Live Response for Servers -off
Live Response unsigned script execution – off
Share endpoint alerts with Microsoft Compliance Center – on
Microsoft Intune connection -on
Authenticated telemetry – on
Preview features – on or off depending if you want to test new features
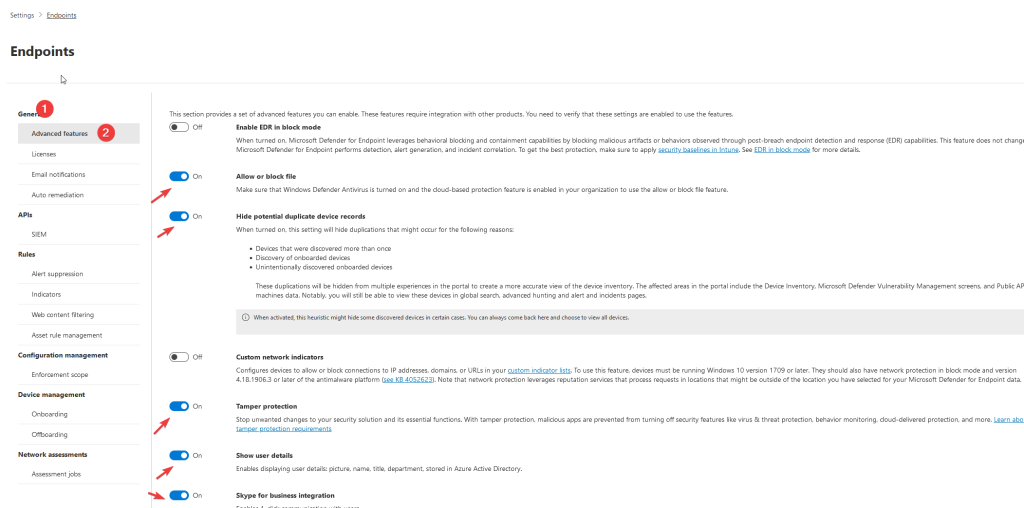
– Next go to -> General -> Email Notifications
Set an administrator Recpients who needs to receive an email for High alert email.
Do the same for the Vulnerabilities tab
See Image below for referance
Onboarding devices
In general, there are now three options:
- Onboard via Azure Arc
- Onboard via Defender for Servers
- Onboard via direct onboarding
In this Guide we use Direct onboarding. There are several methods to direct onboard endpoints.
- Microsoft Configuration Manager
- Intune (Via Tenant-Attach)
- Scripting/ GPO)
- And more..
For Linux the following options are available:
- Script
- Puppet
- Ansible
- Chef
- Saltstack
For now we choose localscript (for learning purposes).
You will find the onboarding packages in the same configuration page.
Go to -> Device management -> Onboarding
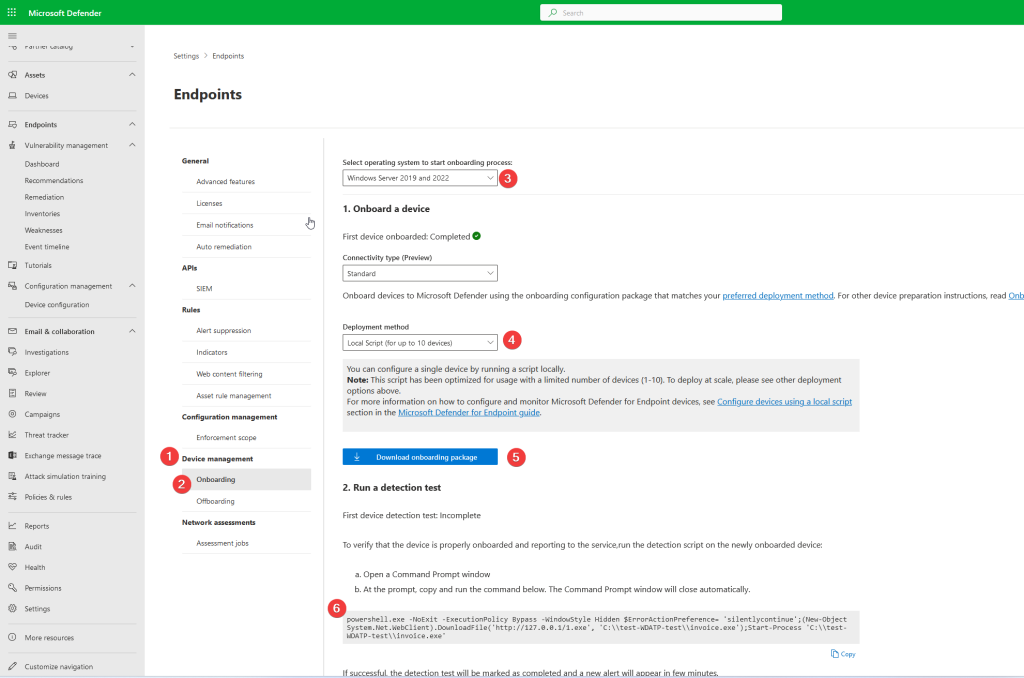
– choose the server or endpoint OS you want to onboard (step 3.)
– choose deployment method (local script) (step 4.)
– Download the onboarding package and save to a safe location (step 5.)
– If you want to test an endpoint if it is onboarded (save the detection test to a .txt file) (step 6.)
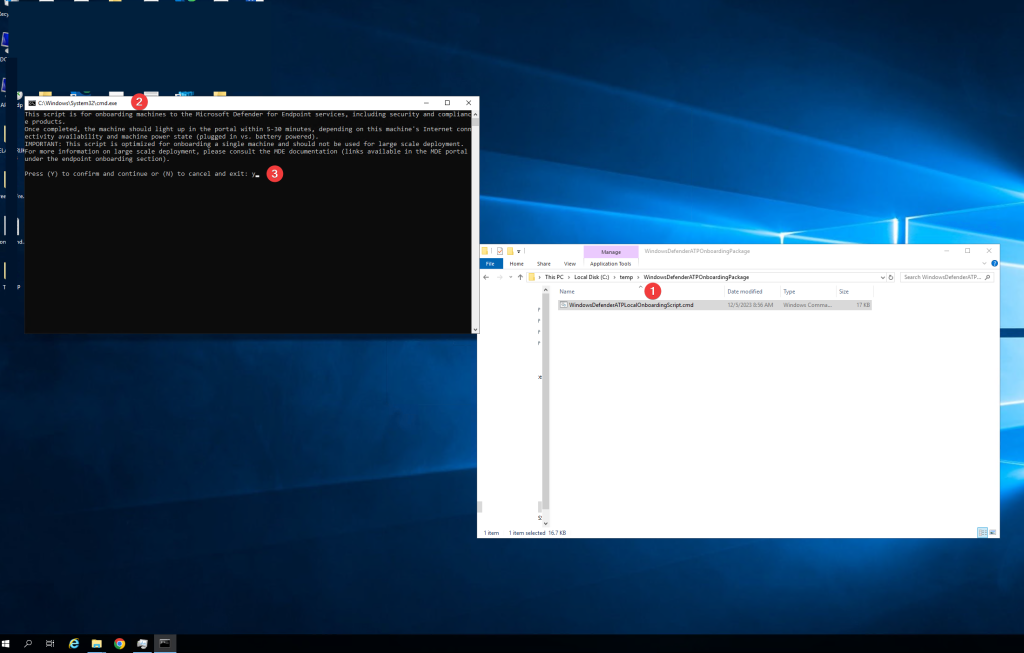
Go to the endpoint that you want to onboard into Microsoft Defender for Endpoint.
extract the zip file in a temp location
execute the .cmd file with administrator privileges.
type “y’ to onboard
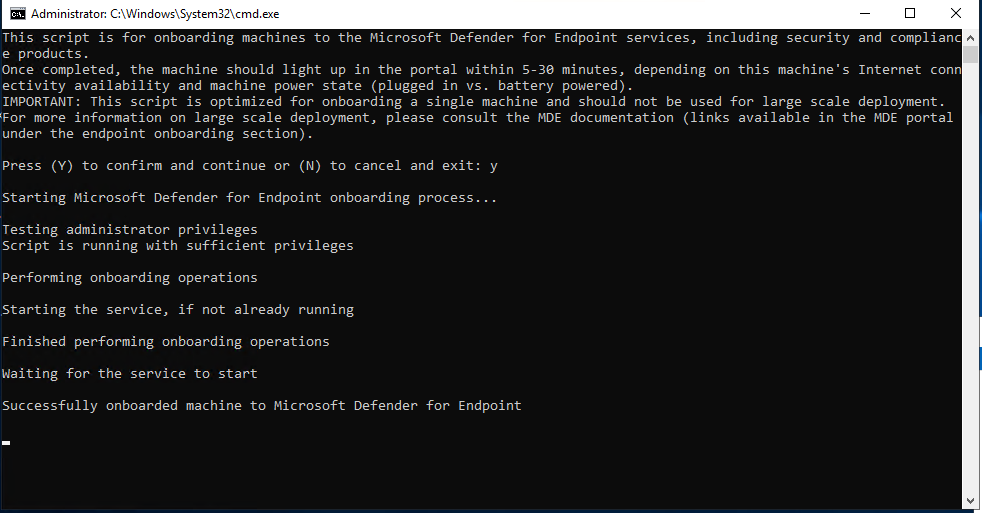
when successful onboarded you see the following message:
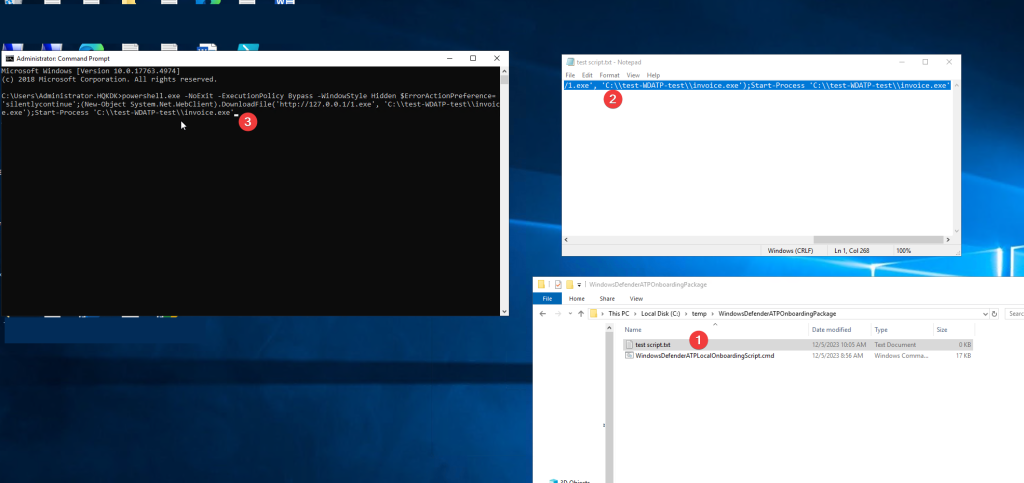
To trigger an alert in the Microsoft defender for endpoint portal.
we use the test script
Microsoft Defender for Endpoint Portal.
In a 10 – 30 minutes you will see your device onboard into Microsoft defender for endpoint
You can find the portal here
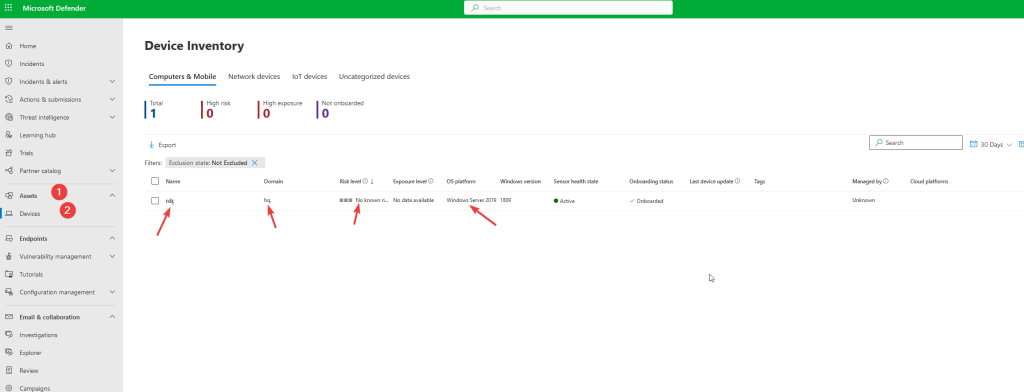
– Go to – assets – Devices
You will see your devicename, the domain, Risk Level, exposure Level, OS platform etc.
Now you are ready to get started with Microsoft defender for endpoint and onboard more devices
Read here why Microsoft for endpoint is a top-tier product in the security market