Category: Microsoft Security
In this blog we’ll write and learn about different features and capabilities of the Microsoft Security Suite.

5 easy ways to Make Microsoft Entra ID Accounts More Secure
The cloud is trending, and more and more applications and services depend on the cloud. A cloud environment offers many advantages but also introduces a number of new risks. Microsoft has sufficient solutions in its services to optimally use this security. Through this article, we will discuss a number of services that are available from…
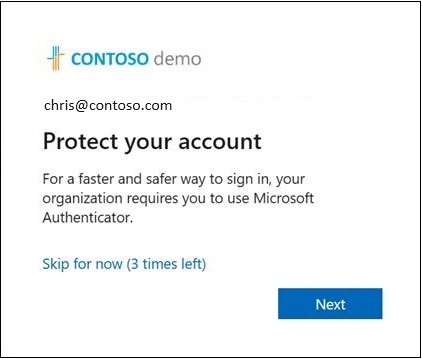
Microsoft MFA – Protect your account pop-up
When a user who can receive Authenticator push notifications hasn’t set it up yet, they’ll be encouraged to set up Authenticator push notifications to make signing in easier and more secure. It’s also possible that they’ll be asked to set up additional security measures. If you use Microsoft Authenticator or another token manager to create…
Common deployment mistakes in Microsoft Defender for Endpoint implementations
When initiating the deployment of Defender for Endpoint, it all commences with thorough preparation. It is crucial to conduct a comprehensive assessment of the existing environment to preempt policy conflicts and meticulously craft a solution that seamlessly aligns with the management methods, systems, and network configuration utilized within that specific environment. What are some of…
Guide – Getting started – Microsoft Defender for Endpoint
The following guide is crafted to assist you in initiating your journey with Microsoft Defender for Endpoint What are the Key Elements of Microsoft defender for endpoint ?Microsoft Defender for Endpoint comprises the following essential elements: Prerequisite Please note that Microsoft Defender for Endpoint has been split into two editions—Plan 1 and Plan 2. Plan…
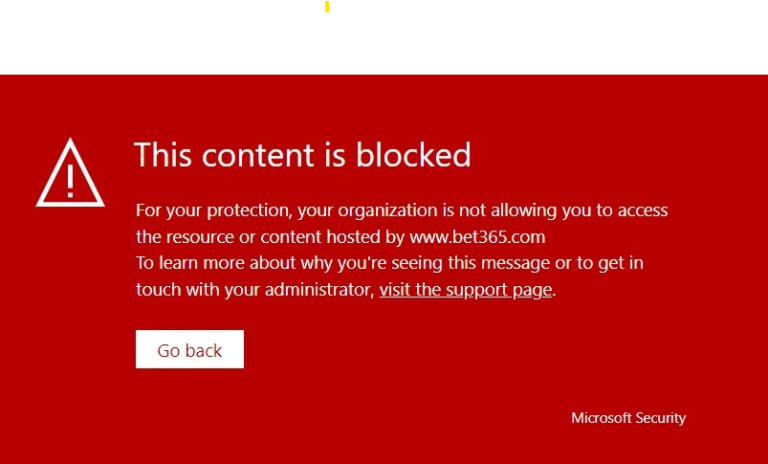
Defender for endpoint – Web content filtering
Defender for Endpoint’s web content filtering is a crucial tool in countering attackers who frequently switch domains, especially when flagged as malicious. AiTM domains, often newly registered and short-lived, can be effectively managed using web content filtering in Microsoft Defender for Endpoint (MDE). Here’s how: With Defender for Endpoint – web content filtering’s help, you…

Defender for Office 365 – Phishing Outlook or Teams (re-do)
Many AiTM scams usually begin with sending messages through platforms like Outlook or Teams, and these messages often contain a dangerous phishing link. To demonstrate how this works, I tested it using a completely new Google Gmail account and included a phishing link associated with AiTM. The AiTM attempt was successfully flagged and identified with…