5 easy ways to Make Microsoft Entra ID Accounts More Secure
The cloud is trending, and more and more applications and services depend on the cloud. A cloud environment offers many advantages but also introduces a number of new risks. Microsoft has sufficient solutions in its services to optimally use this security. Through this article, we will discuss a number of services that are available from Microsoft to better secure Azure Active Directory accounts. The list below is compiled from easy to implement to more difficult to implement
1. Multi-Factor Authentication
In one of our previous articles, we extensively discussed new methods of authentication. This includes simple applications such as Password Protection and Password-less working. The foundation starts with Multi-Factor Authentication (MFA). The identity of a user is extremely valuable to malicious actors, a simple username and password are no longer sufficient, a second factor is needed.
More and more organizations are using Multi-Factor Authentication (MFA). This technique requires, in addition to the use of a password, an additional form of authentication. As a result, the user must always have access to the device to activate the MFA.
Azure MFA can be found in Azure Active Directory. The MFA options can also be combined with security additions such as Password-Less or via a physical security key
2. Conditional Access
Cloud services are globally accessible, making them accessible to malicious actors as well. With Conditional Access, it is possible to protect services based on incoming signals.
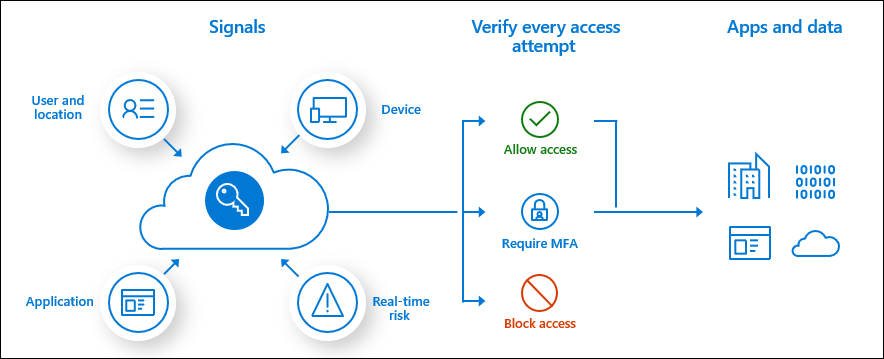
Conditional Access brings together various signals, upon which a policy can be applied.
There are many configurations and policy settings possible – the following are some of the most important for identity protection, but there is a tremendous amount of possibilities when it comes to Conditional Access.
- Enforce MFA for users and apps
- Enforce MFA for admin accounts/roles
- Device/user compliance
- Enforce use of Outlook mail client
- Block legacy authentication: Not all applications use Modern Authentication. When an app is compatible with Modern Authentication, it is suitable for applying MFA/modern authentication.
3. Password Protection through Password Security
Through Password Protection, it is possible to make passwords more secure. Password Protection allows for the configuration of a custom lockout and a lockout threshold. Through an algorithm, commonly used passwords are automatically blocked. It is also possible to create your own list of prohibited passwords, for instance, by blocking words that are frequently used within the organization.
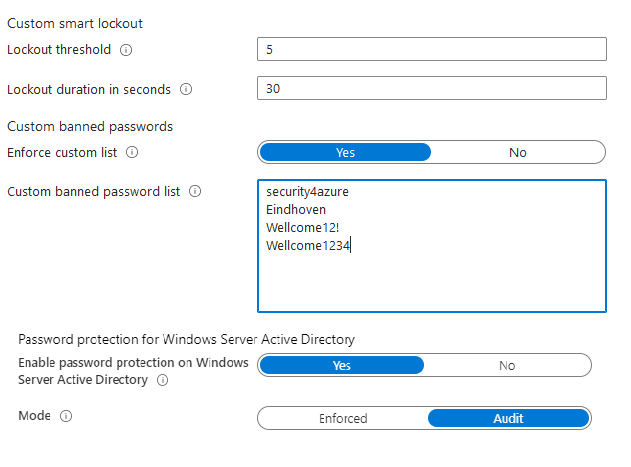
An advantage of Password Protection is that this application can be implemented with almost no extra impact – especially by activating the audit mode to easily observe behavior.
4. Privileged Identity Management
In an organization, securing administrative accounts is the first step. Traditionally, most administrators have a separate admin account. However, this account usually has many roles that are present even outside of working hours. From a security standpoint, this is not ideal, but Privileged Identity Management (PIM) provides a solution.
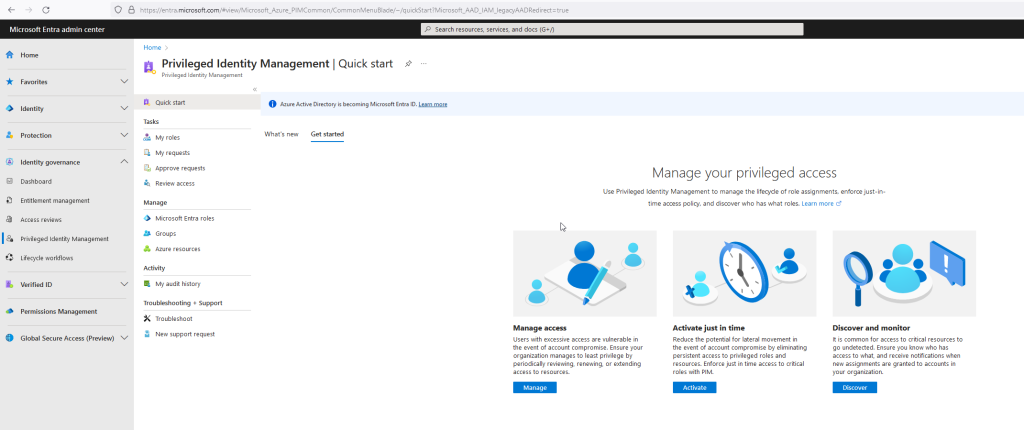
Nowadays, it is strongly advised against permanently assigning high privileges, such as a Global Administrator.
With PIM, all ‘built-in administrative roles’ of Azure and Office 365 can be managed. Then, the user/administrator has the option to activate these roles for a certain period. For each role, a number of configurations are possible, such as the duration, approval from designated individuals, or additional verification through an MFA request.
For each role, it is possible to send a notification when a role is activated and/or to enter a ticket number, so that the activities for the specific role can be tracked.
Applying a ‘Least Privilege’ method offers advantages to the security layer, especially if the times are not set too broadly – if something does happen with the account, the damage is minimal because there are no high privileges present. However, this function requires an Azure AD Premium P2 license.
5. Passwordless sign-in
Passwords are currently still the most commonly used method for logging in. A large portion of online accounts still uses a password. However, we are gradually seeing a shift from a password-based method to a Password-less method.
Microsoft is currently heavily investing in the development of password-less working and the security of your account. For this, Microsoft has introduced various developments to the market, such as the Authenticator app, Windows Hello for Business, and support for security keys.
A common question is why log in without a password when Multi-Factor Authentication is activated? For multi-factor, you still need a password, and it can essentially be seen as a two-step process. It’s always a two-step login.
Windows Hello
Windows Hello is currently the most used solution in the business market for Windows 10 devices. With Windows Hello, it is possible to log in using features such as a PIN, fingerprint, or facial recognition.
Phone Sign-in via Authenticator
The Microsoft Authenticator app is also required for Multi-factor authentication. But since last year, the functionality to log in via Phone Sign-in has been available. With this, you see a code on the website, which you then select in the Authenticator app. Then a biometric authentication is required, such as facial recognition, PIN, or fingerprint.
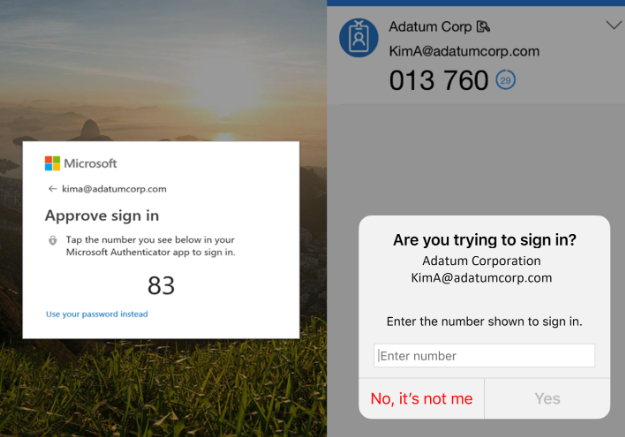
With this, the employee’s identity is verified, and the session will be opened. Especially when we look at user-friendliness, this offers huge advantages – and most importantly, no more passwords.
For the second factor, Phone Sign-in uses facial recognition, fingerprint recognition, or a PIN code set on the device.
